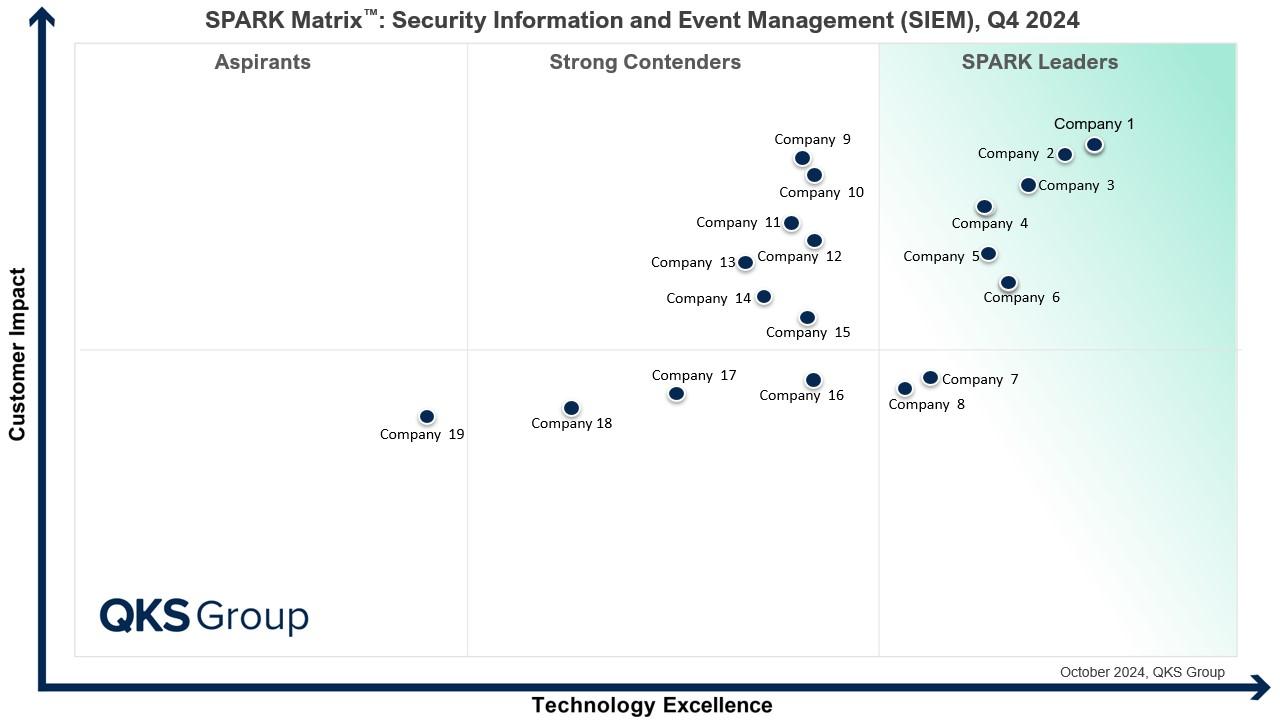
QKS Group’s Security Information and Event Management (SIEM) market research provides a comprehensive global assessment of key vendors, analyzing their product capabilities, core functionalities, and competitive differentiators. This study delivers an in-depth view of the competitive landscape and vendor positioning, empowering technology and service providers with valuable insights to enhance their market understanding and craft strategic, growth-oriented technology roadmaps.
The report features an extensive competitive analysis and vendor evaluation using QKS Group’s proprietary SPARK Matrix™ framework, which ranks and positions leading SIEM vendors based on their technological excellence and market impact. The SPARK Matrix™ analysis includes prominent players such as Cisco (Splunk), Devo, DNIF, Elastic, Exabeam, Fortinet, Google, Gurucul, LogPoint, Logz.io, ManageEngine, Microsoft, NetWitness (RSA), Odyssey CS, OpenText, Rapid7, Securonix, Stellar Cyber, and Sumo Logic.
According to Swathi Suresh, Analyst at QKS Group, “Security Information and Event Management (SIEM) solutions have become foundational to modern cybersecurity frameworks, offering centralized visibility, monitoring, and analysis of security events across diverse IT environments. Over the years, SIEM platforms have evolved from simple log management tools into intelligent, analytics-driven systems that integrate threat detection, behavioral analytics, and automated incident response. By leveraging capabilities such as real-time threat intelligence, User and Entity Behavior Analytics (UEBA), and Security Orchestration, Automation, and Response (SOAR), SIEM solutions enable organizations to proactively detect anomalies, ensure compliance, and mitigate threats before they escalate. In an era of escalating cyber risks and complex digital ecosystems, advanced SIEM platforms serve as a critical enabler of resilience, agility, and proactive defense.”
The global SIEM market is experiencing rapid transformation, fueled by the increasing sophistication of cyberattacks, expanding cloud environments, and the growing need for real-time security visibility. Organizations are adopting AI- and ML-driven SIEM platforms to detect threats faster and automate incident responses, reducing mean time to detect (MTTD) and mean time to respond (MTTR). The integration of machine learning algorithms enables continuous behavioral analysis of users and entities, allowing SIEM solutions to identify subtle deviations from normal patterns that may indicate insider threats or advanced persistent attacks (APTs). As businesses move toward hybrid and multi-cloud infrastructures, cloud-native SIEM deployments are gaining momentum due to their scalability, agility, and ability to correlate data across distributed environments.
QKS Group defines Security Information and Event Management (SIEM) as a set of tools or a solution that detects and tracks data breaches by analyzing and integrating logs and event data from multiple sources, including connected devices, servers, networking devices, and more. SIEM provides a holistic view of an organization's data, information, network, or cybersecurity in real-time, by correlating and analyzing data from various sources. Additionally, it allows organizations to proactively identify and respond to security threats and ensure the security of their IT infrastructure.
#SIEM #SecurityInformationAndEventManagement #CyberSecurity #ThreatDetection #SecurityAnalytics #SPARKMatrix #SecurityInnovation #RiskManagement